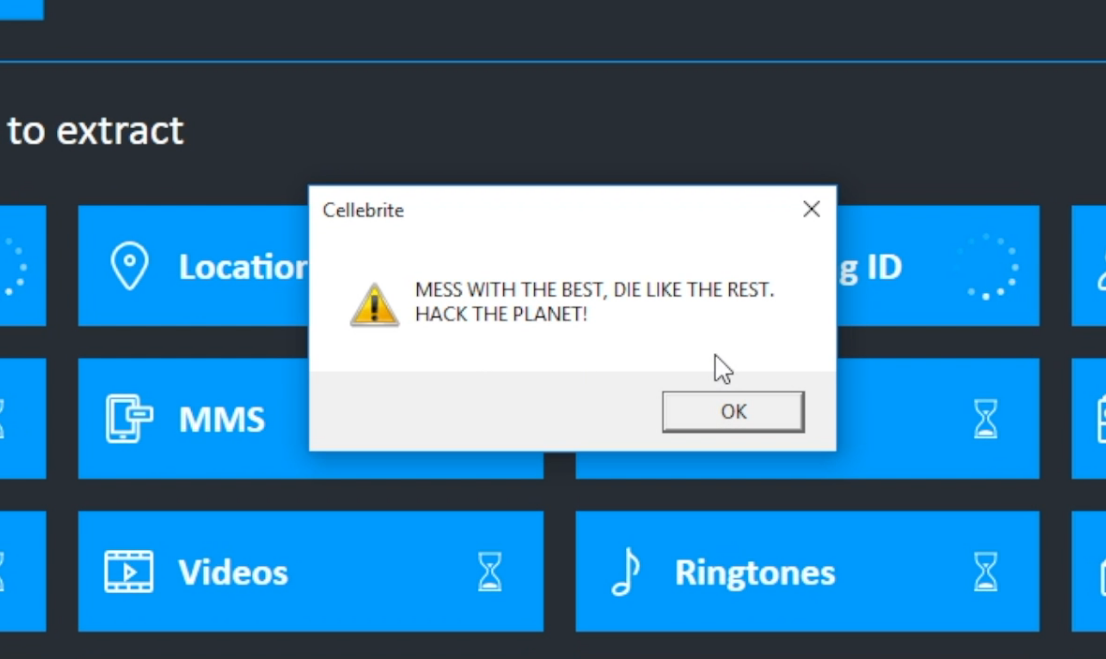
Phone scanning and data extraction company Cellebrite is facing the prospect of app makers being able to hack back at the tool, after Signal revealed it was possible to gain arbitrary code execution through its tools.
Cellebrite tools are used to pull data out of phones the user has in their possession.
"By including a specially formatted but otherwise innocuous file in an app on a device that is then scanned by Cellebrite, it's possible to execute code that modifies not just the Cellebrite report being created in that scan, but also all previous and future generated Cellebrite reports from all previously scanned devices and all future scanned devices in any arbitrary way (inserting or removing text, email, photos, contacts, files, or any other data), with no detectable timestamp changes or checksum failures," Signal CEO Moxie Marlinspike wrote.
"This could even be done at random, and would seriously call the data integrity of Cellebrite's reports into question."
Usually, when vulnerabilities of this type are found, the issue is disclosed to the maker of the software to fix, but since Cellebrite makes a living from undisclosed vulnerabilities, Marlinspike raised the stakes.
"We are of course willing to responsibly disclose the specific vulnerabilities we know about to Cellebrite if they do the same for all the vulnerabilities they use in their physical extraction and other services to their respective vendors, now and in the future," he said.
The Signal CEO said that Cellebrite contains "many opportunities for exploitation" and he thought they should have been more careful when creating the tool.
For instance, Cellebrite bundles FFmpeg DLLs from 2012. Since that year, FFmpeg has had almost 230 vulnerabilities reported.
Marlinspike also pointed out that Cellebrite is bundling two installers from Apple to allow the tools to extract data when an iOS device is used.
"It seems unlikely to us that Apple has granted Cellebrite a license to redistribute and incorporate Apple DLLs in its own product, so this might present a legal risk for Cellebrite and its users," he said.
In a video dripping with references to the movie Hackers, Marlinspike showed an exploit in action, before rattling a sabre in the direction of Cellebrite.
"In completely unrelated news, upcoming versions of Signal will be periodically fetching files to place in app storage. These files are never used for anything inside Signal and never interact with Signal software or data, but they look nice, and aesthetics are important in software," he said.
"We have a few different versions of files that we think are aesthetically pleasing, and will iterate through those slowly over time. There is no other significance to these files."
Marlinspike said he was incredibly lucky to have found a Cellebrite tool package laying on the ground while going for a walk.
In December, Marlinspike lashed out at Cellebrite claims that it could crack Signal's encryption.
"Cellebrite posted something with a lot of detail, then quickly took it down and replaced it with something that has no detail," Marlinspike wrote at the time.
"This is not because they 'revealed' anything about some super advanced technique they have developed (remember, this is a situation where someone could just open the app and look at the messages). They took it down for the exact opposite reason: it made them look bad.
"Articles about this post would have been more appropriately titled 'Cellebrite accidentally reveals that their technical abilities are as bankrupt as their function in the world.'"
Related Coverage
from Latest Topic for ZDNet in... https://ift.tt/3dG2XTG
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.