1. Abstract
Automated license plate recognition systems have been used for over a decade by law enforcement to monitor and identify traffic offenders. More recently, the technology has found its way to customer-facing applications, despite criticism by privacy advocates. Until now, most privacy concerns revolved around increased risk of government surveillance, automated decision making, high cost of usage and potential data breaches. With this research paper, we are putting the theory into practice and factual data, uncovering different ways in which these systems are inadvertently already exposing vehicle location data to the general public. The growing trend of affected license plate systems across Europe and the U.S. is concerning, and calls for prompt and decisive actions by legislators to mitigate the increasing risks.
From June 2022 to mid-September 2022, a group of 120 randomly selected individuals with different levels of car usage volunteered to have their license plates tracked as part of this study. None of the participants were briefed about the research methodologies, so their participation would not influence their driving behavior.
One discovered methodology involved (re-)registering the license plates into parking and toll road applications that start- and stop sessions based on automatic license plate recognition. Out of the 120 license plates monitored, we were able to track down the live location of slightly over 29% of vehicles during a 100-day window (26.5% of which using methodology #1, and additional 2.5% using methodology #2 which was tested on a smaller scale).
Another technique was proven to work in areas without cameras, such as on-street parking in cities and residential neighborhoods. A proof-of-concept stalkerware application was developed to routinely create one-second parking sessions for a multitude of parking zones across the country, intercepting any errors that would indicate the vehicle is already parked there. When used in areas that offer limited free parking time, the scan would only have to run once a day and would not incur any charges for the attacker.
The attack surface of both techniques is widespread, with more 3,850 affected areas identified in 10 different countries in Western Europe. All traffic participants can be affected, regardless of whether they already use parking apps or not. Other than avoiding all affected areas, the only way for road users to temporarily mitigate the risk is to invoke their (UK/EU) GDPR’s Right to Restrict Processing on the concerned data processors. In order to facilitate this, a web application hosted at NOTMYPLATE.COM was developed to help users send in a propper GDPR request for their license plate with an up-to-date list of affected parking apps.
While this will help combat the privacy loopholes short-term, a more rigid solution will need to be put into place by data processors and regulators.
2. Tracking methodologies
The COVID-19 pandemic has accelerated the rise of contactless solutions, and the parking industry is no exception to this trend: ticketless entry through a mobile app or license plate recognition have become a standard for the large majority of parking operators. This trend increases convenience for its end-users, but also inadvertently exposes these previously closed systems to remote attacks described in the following sections.
2.1. Session hijacking through ANPR cameras
2.1.1. Technique overview
In order to automatically start- and stop a parking- or tollroad session based on a license plate, parking apps allow their users to enter their license plate number. Whilst this is convenient, this system lacks any form of authorisation: none of the apps verified whether the license plate was owned or affiliated to the person who entered it. This creates an opportunity window for a malicious actor to register someone else’s license plate and enable ANPR-based payments on their behalf. The next time a connected ANPR camera would detect the license plate, the attacker would receive a live push notification informing them of their session, disclosing the name of the parking lot the license plate is detected.
2.1.2. Study results
On May 31 2022, we launched a call on Twitter and Instagram to sign up participants for our car-tracking experiment. To be eligible to participate, the individuals had to be a named driver of the car, but there were no requirements in terms of car usage. None of the individuals that agreed to participate were briefed about the tracking methodologies, to ensure their driving behavior would not change. In total, 120 participants had their license plates entered in the apps of two selected parking operators: Q-Park and Indigo. The third big Belgian operator Interparking was excluded because their application only allows its users to link one license plate at a time, which is less convenient for a large scale experiment.
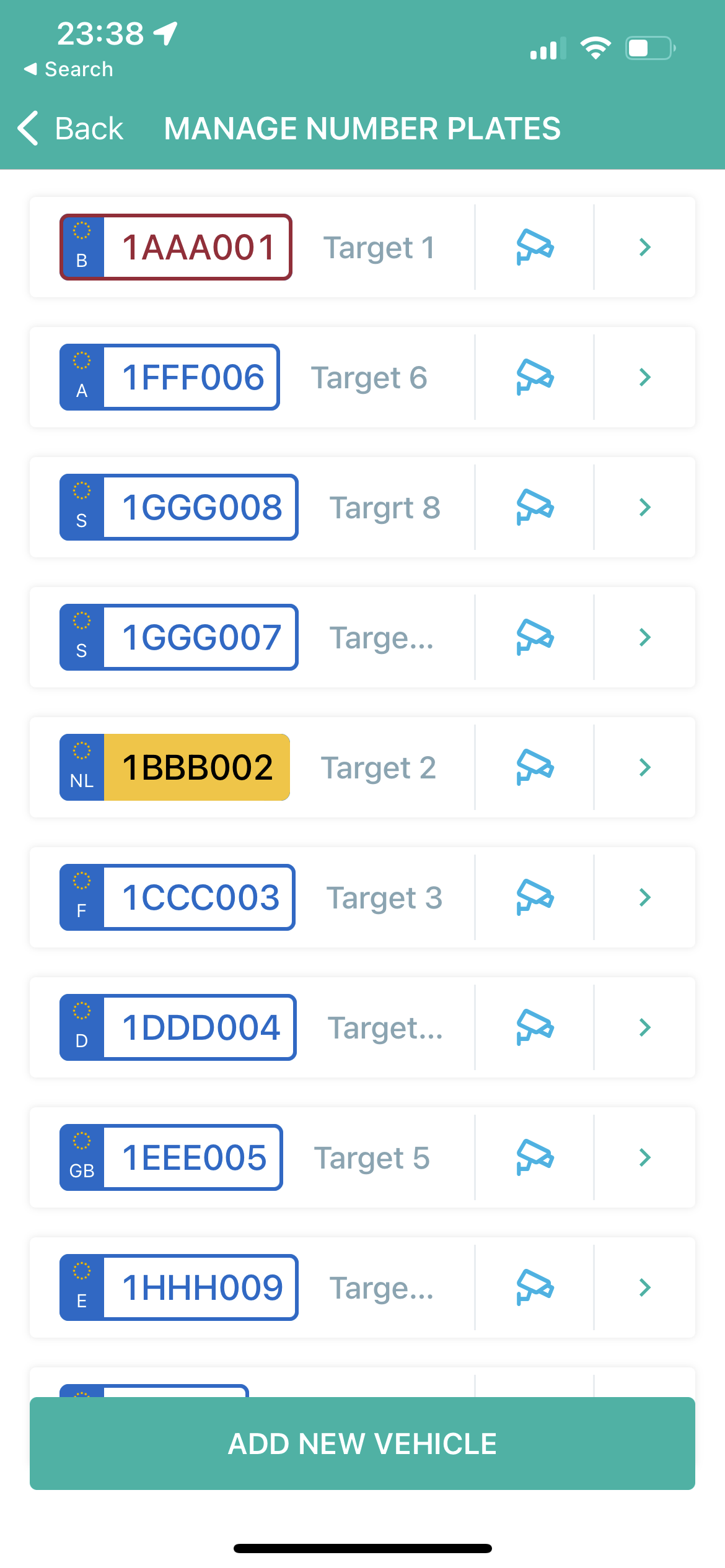

Entering hundreds of plates in 4411 (Q-Park) and Indigo Neo (OPnGO)
(real license plates replaced with fake ones for the screenshots)
Within the first days of the experiment, we already received the first succesful hits: one in a Q-Park location near a hospital in Antwerp, and one in an Indigo location in Malines. 
Over the duration of the experiment, the list of successfully located vehicles continued to grow in a linear fashion. After 100 days, 26.5% of all vehicles were already successfully located using this methodology:
After every successful match, we deactivated or removed the license plate in the system to prevent suspicion. In many cases, the matched location would provide insights into the activity the targeted driver was attending while the vehicle was parked. Amongst the parking locations are hospitals, shopping malls, casino’s, swimming pools, concert venues, public transportation hubs or offices. Given enough data points, it could be possible to deanonymize individuals based on their activity history.
2.1.3. Attack operation costs
As the attacker is creating ANPR-based sessions on behalf of their victims, it does require them to cover the parking fee in case of a successful attack. The exact amount would depend on the location and the duration of the session, but typically be only a fraction of the costs of other tracking techniques, such as hidden trackers or private investigators.
During the investigation, €273.85 was spent on parking tickets ranging from €1,60 to €36,00. Some sessions were not charged because the driver either immediately left the building, or a technical error occurred. The average cost to successfully track down a vehicle was €7,82.
In a real-world attack scenario, attackers may reduce operating costs by cutting the parking session short through the customer service or using stolen credit cards. On some occasions, the unknowing victim would still grab a ticket and pay for it themselves, reducing the cost of the attack down to zero.
2.1.4. Possible mitigations
Since the technique attacks the fundamentals of license plate based parking systems, it is not possible to fully mitigate the attack without losing some of its current convenience and functionalities.
2.1.4.1. Asking for proof of plate ownership
While license plate owner verification would seem like a logical solution to implement, it brings a couple of hurdles with it. Having users upload their registration certificate does not only diminish the user experience, it would provide the parking operators with even more sensitive data they are not permitted to process, and could easily be forged.
2.1.4.2. Blocking re-registration (plate hijacking)
Our research has shown that the majority of parking apps allow re-registration of license plate, even if the plate is already listed in the system. Without any notification or need for confirmation, the license plate would be disabled from the victim account and any future charges or notifications regarding the license plate would be sent to the attacker.
Some applications do prevent the re-usage of a license plate through their application. In that case, the customer service could possibly still re-assign it when contacted.
2.1.4.3. Reducing the amount of plates that can be added to a single user
Some parking apps allowed an infinite amount of license plates to be added to their ANPR payment list, allowing attackers to conduct surveillance on scale. Reducing the amount of license plates one could add would make the attack less convenient in execution, but would not remediate the issue. The downside of a limitation is that some businesses and organizations already use these parking apps to manage their entire fleet.
2.1.4.4. Implementing an opt-out list
Just like a robinson list, a centralized blacklist can be maintained for people who wish to opt-out from private companies processing their license plate date. This would however not protect people that are unaware of the risk, and would have to be maintained by an authorized and trusted body. It only works if all the apps decide to implement it.
2.1.4.5. Only allowing license plate recognition for pre-booked slots
While limiting automatic license plate recognition based billing to slots that are pre-booked by a user does not prevent malicious actors from verifying whether a vehicle has been somewhere during a specific period of time, it makes a wide scale operation costly and less feasible.
2.1.4.6. Showing and confirming ANPR payment details warning upon entry
The attack in its current form raised little to none suspicion for most test subjects, given the fact that a barrier that opens automatically is not an uncommon thing to see at a parking lot. Had the screens at the entry informed them about the ANPR session along with the payment information that did not match theirs, it would not have gone unnoticed.
2.1.4.7. Secondary authentication with an RFID tag
Certain tollroad systems, such as France's Bip & Go télépéage, require a physical Radio-frequency identification (RFID) tag to be present in the car for authentication purposes. Linking online payments to a secure tag ID rather than a license plate may still allow the convenience of a seamless enterance and prevent others accessing or registering the account.
2.2. Trial-and-error attacks with free limited parking
2.2.1. Methodology overview
As sustainable urban mobility planning is reclaiming street parking spots for public use, parking control solutions make their way onto public space. Since placing ANPR cameras on the corner of every street would be excessive and expensive, drivers are required to enter their license plate into a parking app- or meter upon arrival in a parking zone. Next to paid on-street parking, this allows cities to offer free parking for a limited time, e.g. 30 minutes for free near a shopping district. To prevent drivers from continuously renewing their free parking slot, parking operators implement a cooldown period in which a free parking session can no longer be created for a license plate. In most cases, a free slot can only be used once a day. When entering license plates for vehicles that are already registered or used their free slot for that day, parking applications would typically show an error that a session cannot be created. Attackers can use this error as an oracle to determine who has already parked there, by entering their license plates into the system and checking whether the error shows. 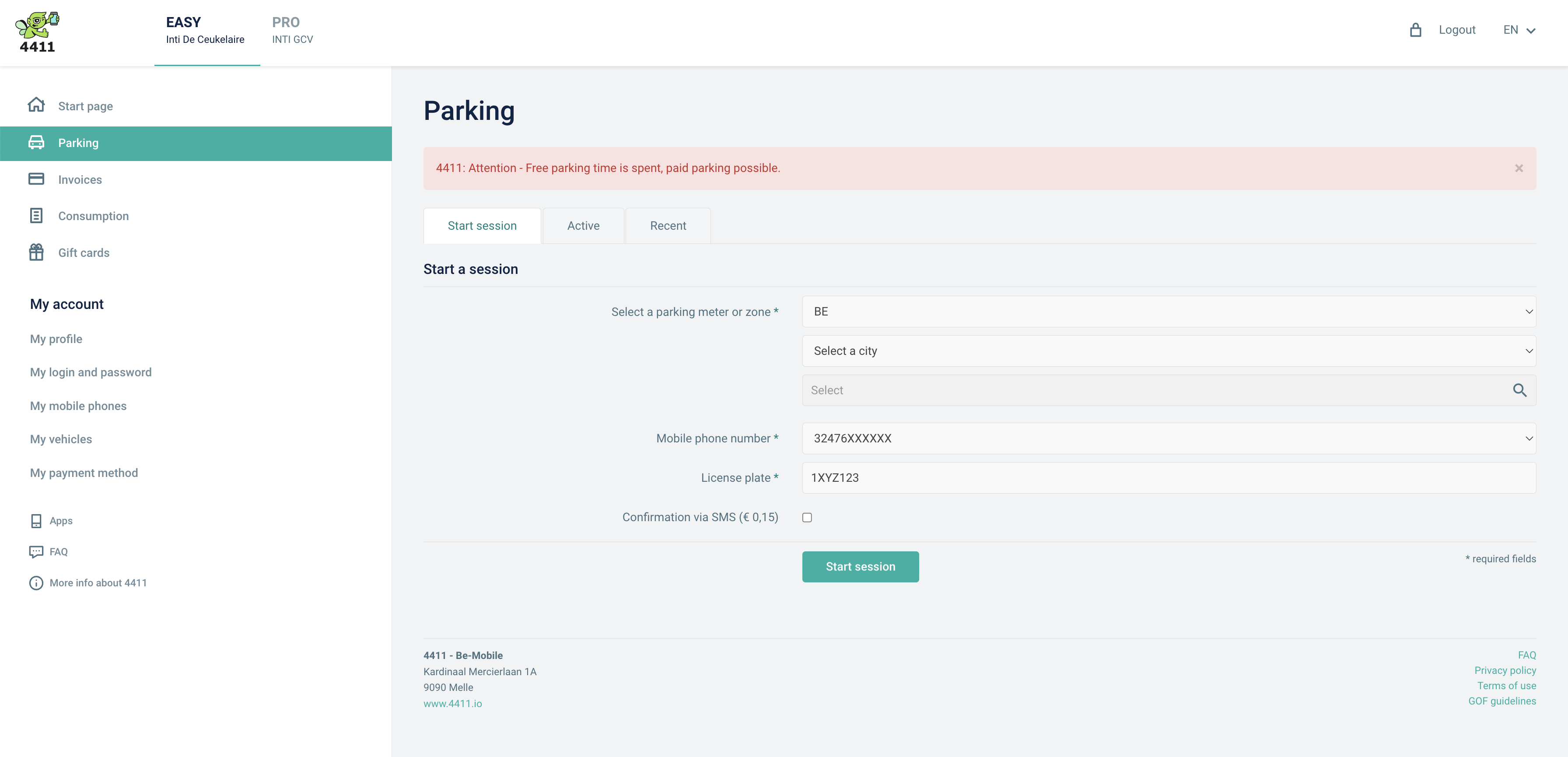 Parking apps like 4411 may show an error if a license plate has already consumed a free parking slot.
Parking apps like 4411 may show an error if a license plate has already consumed a free parking slot.
In order to exploit this technique at a scale, attackers can create an automated system that poll for the presence of a certain license plate across all parking zones on a regular basis. For this study, a proof-of-concept stalkerware application was created for the 4411.io parking app, active in Belgium and The Netherlands. The system would simulate a normal Android application and automatically create 1-second parking sessions for selected license plates on a daily basis:
If the free parking session could not be created because the user had already parked there, the system would catch this error:
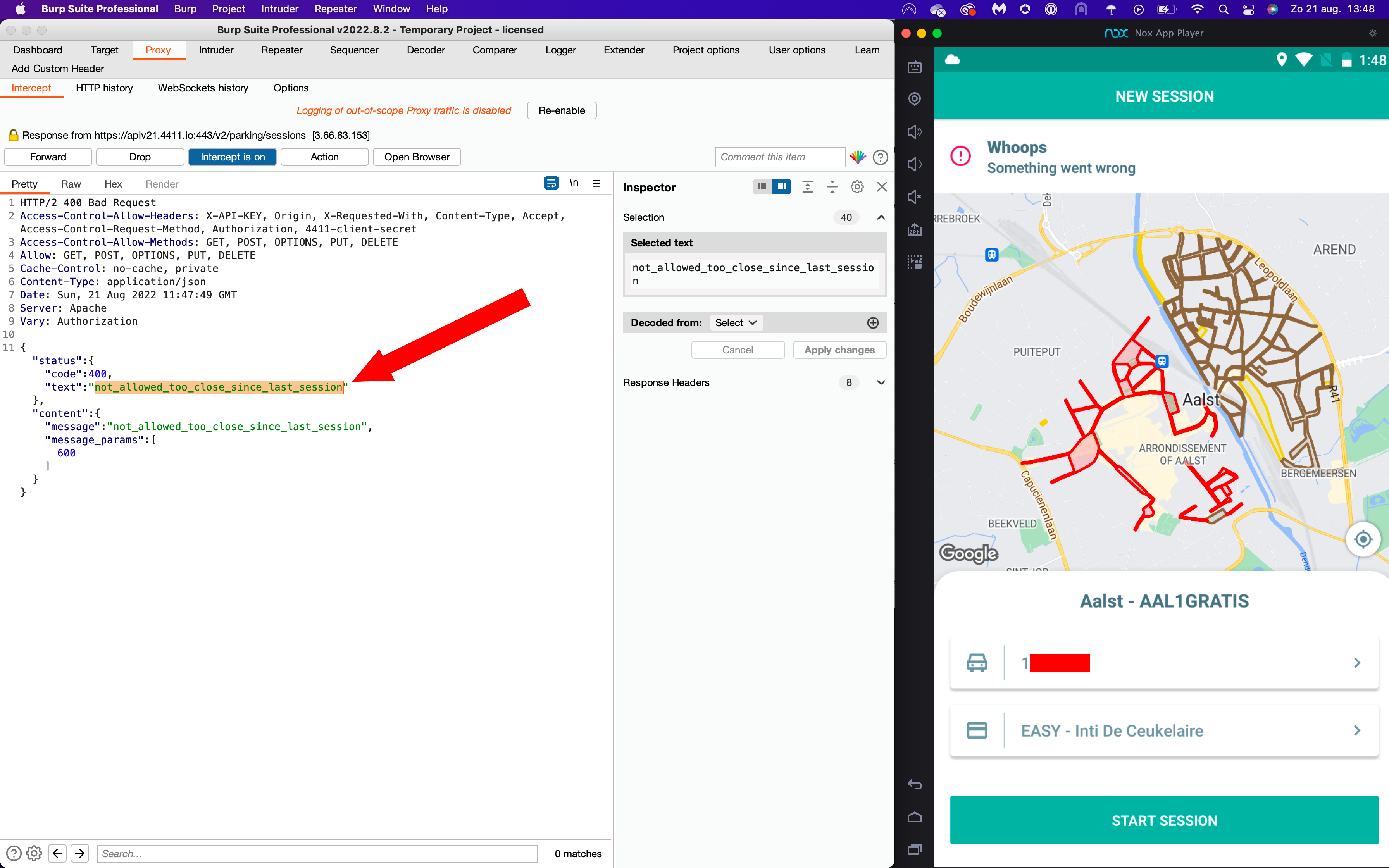 Mobile application returning NOT_ALLOWED_TOO_CLOSE_SINCE_LAST_SESSION error for a license plate
Mobile application returning NOT_ALLOWED_TOO_CLOSE_SINCE_LAST_SESSION error for a license plate
To avoid suspicion by the targets, the parking sessions were automatically created just before the free slots were reset, so they would never arrive at a parking spot to find out that someone had created a session on their behalf. If the error was captured, a push notification would be sent to the attacker to inform them about a successful hit: 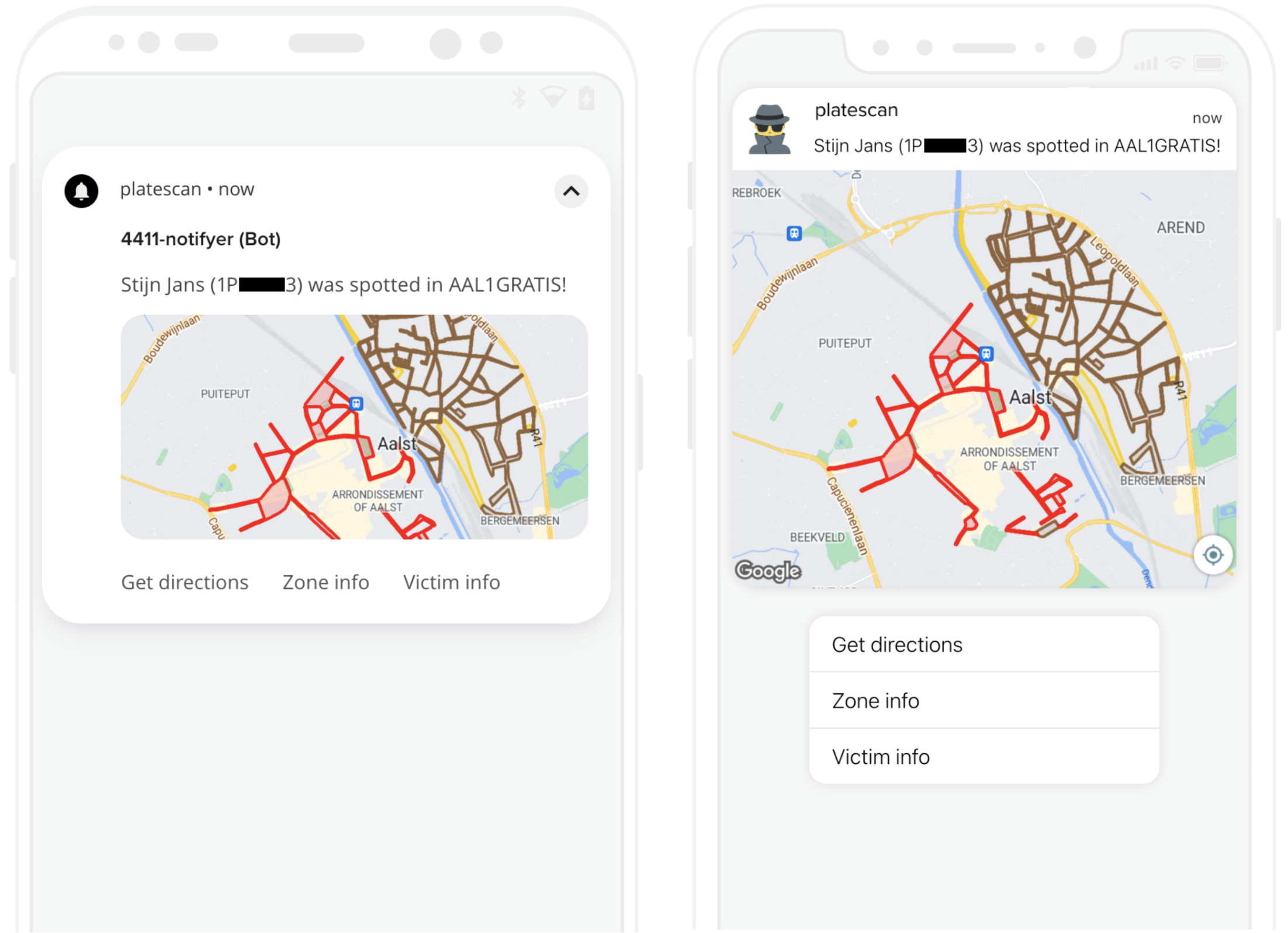 Once a consumed free parking slot is detected, the system sends a push notification to the phone of the attacker.
Once a consumed free parking slot is detected, the system sends a push notification to the phone of the attacker.
This technique is less suited for mass-surveillance as it requires the application to create a considerable amount of parking sessions per target, increasing the chances of being detected by the parking operator. In the limited proof of concept, 19 participants from a selected city implementing this system were tracked over a period of 100 days. Three inhabitants were detected in the monitored zones, all of which multiple times. The system created more than 5,000 parking sessions in a clearly automated pattern, but was never blocked from operating by the parking operators.
Platescan demo:This video shows how the PlateScan is able to detect that I have used a free parking slot today, by attempting to create another free parking session at the end of the day. If the system sees that the license plate has already used its free time, it sends a notification to my mobile phone.
The license plate is fake for the purpose of the video.
2.3. Authentication by plate in parking apps
Some parking applications offer the possibility to pay or download receipts containing location details merely by supplying the license plate on the website, enabling attackers to monitor locations for on- and offstreet parking sessions.
2.3.1. Example: APCOA Connect / PayByPhone (UK / IE)
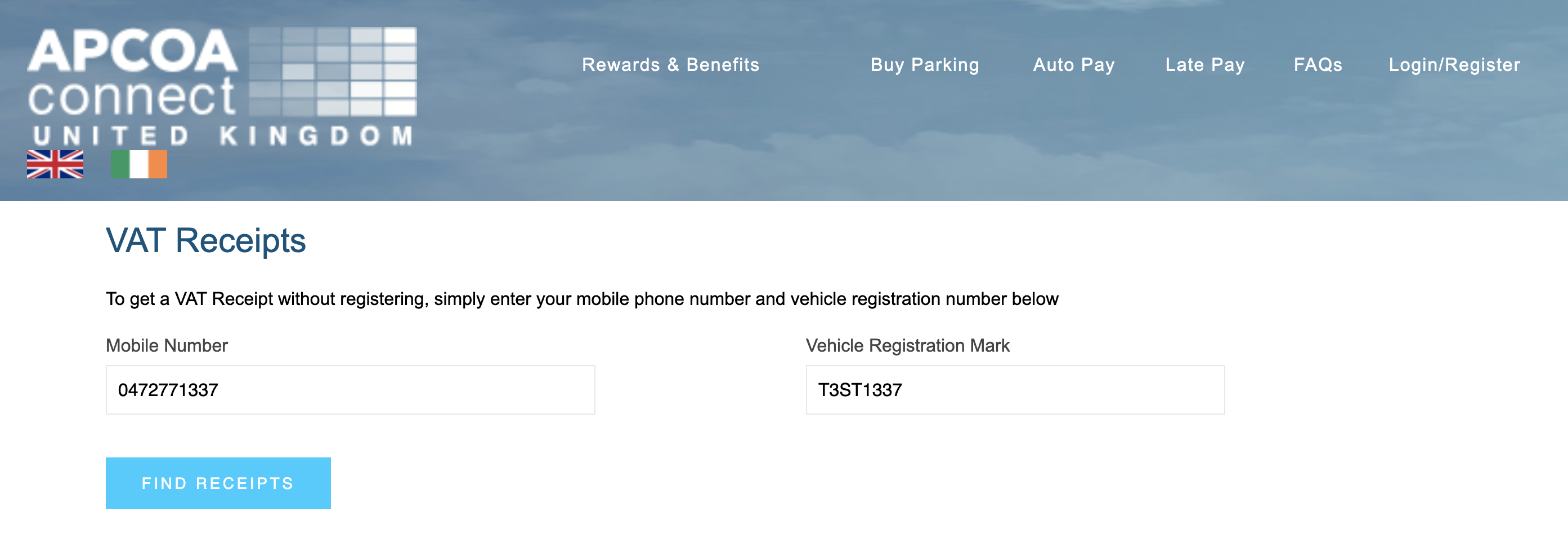
APCOA Connect offers its users the possibility to download VAT receipts containing the exact time and location of parking sessions merely by specifiying a license plate and a phone number. Attackers could use public data sources to get the phone number of a victim, such as the Facebook data breach in order to get an overview of their location details.
Live demo For demonstration purposes, I have created a parking session with the following details:
| Phone number: | 0472771337 |
| License plate: | T3ST1337 |
Anyone navigating to https://www.apcoaconnect.com/receipts can enter my details and query my location info. A system designed to poll for this information periodically could get a real-time overview of my parking sessions:
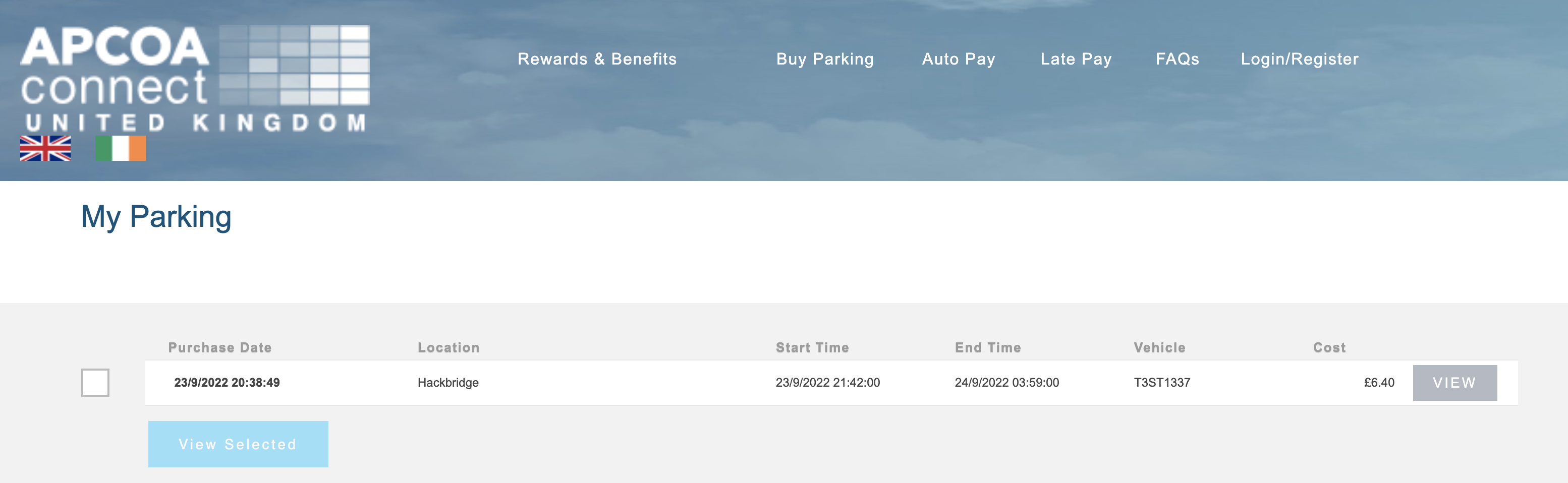
Everyone can see I started a parking session at Hackbrigdge at 23/09/2022 21:42 local time
2.3.2. Autopay
Autopay.io is a platform active in Norway, Sweden, Denmark and Finland and Germany. Just like described in "2.1. Session hijacking through ANPR cameras", it utilizes ANPR recognition to automacally debit parking costs for a parking session:  Their website features a form that allows users to query unpaid parking sessions for the past 48 hours, and pay for them:
Their website features a form that allows users to query unpaid parking sessions for the past 48 hours, and pay for them: 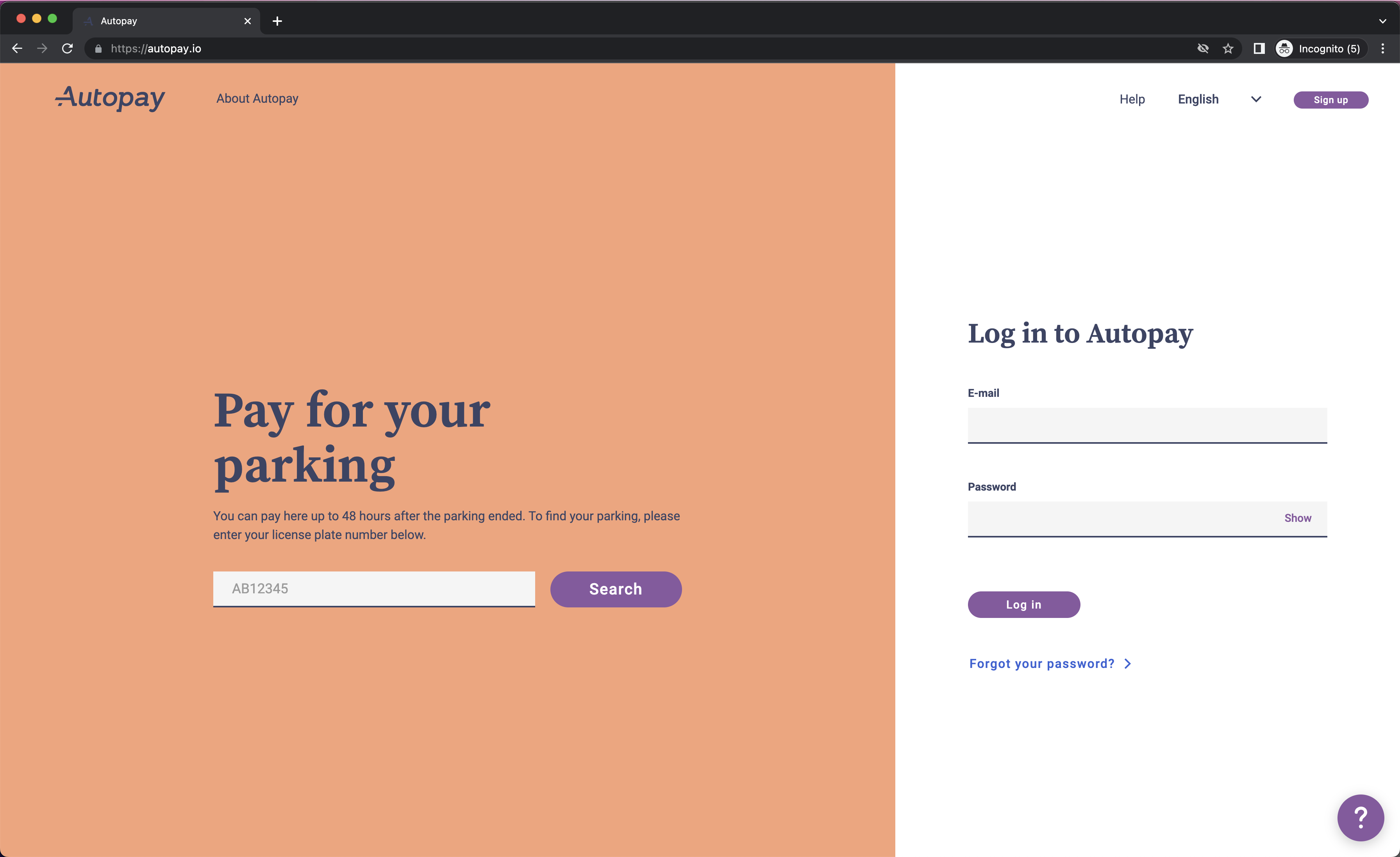 At first glance, the absence of (re)captcha technologies indicates that an attacker could simply run a script to run this every 48 hours to continously monitor a license plate.
At first glance, the absence of (re)captcha technologies indicates that an attacker could simply run a script to run this every 48 hours to continously monitor a license plate.
3. Affected apps & operators in Europe
We have analyzed the most popular B2C parking applications utilizing ANPR technologies. None of the tested apps implemented mechanisms to validate whether the application user was the legitimate license plate owner. Note that we were only able to test and validate ANPR functionalities in Belgium. Some parking operators may not have rolled out number plate recongnition in all territories yet. Please check the local website to see if they've already rolled out ANPR parking in your area. We still included them in the list, as a request for restriction of processing may also apply to planned implementations.
Overview per country
| Country | Operators |
|---|---|
| Austria 🇦🇹 | EasyPark, Interparking, APCOA |
| Belgium 🇧🇪 | EasyPark, Q-Park, Indigo Neo, Interparking, APCOA |
| Denmark 🇩🇰 | EasyPark, Q-Park, APCOA, AutoPay |
| Finland 🇫🇮 | EasyPark, AutoPay |
| France 🇫🇷 | Q-Park, APCOA, Indigo Neo, Interparking |
| Germany 🇩🇪 | EasyPark, Q-Park, Contipark, APCOA, AutoPay |
| Hungary 🇭🇺 | EasyPark |
| Iceland 🇮🇸 | Easypark |
| Ireland 🇮🇪 | Q-Park, APCOA |
| Italy 🇮🇹 | EasyPark, Interparking, APCOA |
| Liechtenstein 🇱🇮 | EasyPark |
| Luxembourg 🇱🇺 | Indigo Neo |
| Montenegro 🇲🇪 | EasyPark |
| Netherlands 🇳🇱 | EasyPark, Q-Park, Indigo Neo, Interparking, APCOA |
| Norway 🇳🇴 | EasyPark, APCOA, AutoPay |
| Poland 🇵🇱 | Interparking, APCOA |
| Portugal 🇵🇹 | EasyPark |
| Romania 🇷🇴 | Interparking |
| Serbia 🇷🇸 | EasyPark |
| Slovenia 🇸🇮 | EasyPark |
| Spain 🇪🇸 | EasyPark, Indigo Neo, Interparking, AENA |
| Sweden 🇸🇪 | EasyPark, APCOA, AutoPay |
| Switzerland 🇨🇭 | EasyPark, Twint+ / ParkingPay |
| United Kingdom 🇬🇧 | EasyPark, Q-Park, APCOA, NCP |
3.1. EasyPark (CameraPark) / ParkMobile (ex-ParkNow Group)
Active in: 🇸🇪 SE, 🇳🇴 NO, 🇩🇰 DK, 🇫🇮 FI, 🇮🇸 IS, 🇬🇧 UK, 🇺🇸 US, 🇩🇪 DE, 🇫🇷 FR, 🇳🇱 NL, 🇧🇪 BE, 🇪🇸 ES, 🇮🇹 IT, 🇨🇭 CH, 🇦🇹 AT, 🇵🇹 PT, 🇸🇮 SI, 🇦🇺 AU, 🇳🇿 NZ, 🇷🇸 RS, 🇲🇪 ME, 🇱🇮 LI, 🇭🇺
HU Mobile app: Android iOS Contact: [email protected] Steps to track a target:- Install the EasyPark app and create an account
- Click the menu icon (☰), tap payment and add a payment method
- Click the menu icon (☰), tap vehicles and add your target's license plate
- Click the menu icon (☰), tap CameraPark and select your target's vehicle to enable tracking
- All set! You are now able to intercept (and pay for) your victim's parking sessions in real-time, disclosing their location
3.2. Q-Park
Active in: 🇳🇱 NL , 🇩🇪 DE, 🇧🇪 BE, 🇬🇧 UK, 🇫🇷 FR, 🇮🇪 IE, 🇩🇰
DK Mobile app: Android iOS Contact: [email protected] Steps to track a target:- Install Q-Park's mobile application on your device
- In Profile > Payment methods, click Add payment method and enter your details
- In Profile > Number plates, enter the target's license plate. Make sure to select the correct country
- In Products > Pay as you Go Parking (alternatively named mobile parking), link the target's license plate.
- All set! You are now able to intercept (and pay for) your victim's parking sessions in real-time, disclosing their location
3.3. Indigo Neo (OPnGO)
Active in: 🇧🇪 BE, 🇫🇷 FR, 🇪🇸 ES, 🇱🇺
LU Mobile app: Android iOS Contact: [email protected] Steps to track a target:- Install the Indigo Neo application on your device
- Go to My account > Cards and add your credit card
- Go to My account > Vehicles and add your target's license plate
- Go to My account > On demand access and press enable
- All set! You are now able to intercept (and pay for) your victim's parking sessions in real-time, disclosing their location
3.4. Interparking / Contipark
Active in: 🇦🇹 AT, 🇫🇷 FR, 🇩🇪 DE, 🇮🇹 IT 🇳🇱 NL, 🇵🇱 PL, 🇧🇪 BE, 🇷🇴 RO, 🇪🇸
ES Web application (BE): https://www.parkingmadeeasy.be Contact: [email protected] Steps to track a target:- First, order a PCard+ from your local Interparking website
- Navigate to https://www.parkingmadeeasy.be (Belgium) and login with your PCard+ details
- Click Add new license plate, and add the license plate number of your victim
- All set! You are now able to intercept (and pay for) your victim's parking sessions in real-time, disclosing their location
3.5. APCOA
Active in: 🇦🇹 AT, 🇧🇪 BE, 🇩🇰 DK, 🇩🇪 DE, 🇮🇪 IE, 🇮🇹 IT, 🇱🇺 NL, 🇳🇱 NL, 🇳🇴 NO, 🇵🇱 PL, 🇸🇪 SE, 🇨🇭 CH, 🇬🇧
UK Apcoa flow app: Android iOS Contact: [email protected] Steps to track a target:- Install the APCOA Flow app on your mobile device
- Create an account
- Add your vehicle license
- Setup your payment method
- All set! You are now able to intercept (and pay for) your victim's parking sessions in real-time, disclosing their location
- Go to apcoaconnect.com
- Log in or create an account
- Under payment details, fill in your credit card details
- Go to Auto pay > Vehicle details and scroll down to "Add new vehicle"
- Enter the target's vehicle details (pick anything for make and colour)
- Go to Auto pay > Autopay details > Register for autopay and sign up the vehicle for all contracts
- All set! You are now able to intercept (and pay for) your victim's parking sessions in real-time, disclosing their location
3.6. Autopay.io
Active in: 🇳🇴 NO, 🇸🇪 SE, 🇫🇮 FI, 🇳🇴 DK, 🇩🇪
DE Webapp: AutoPay.io Contact: [email protected] Steps to track a target:- Go to autopay.io
- Go to the vehicles section
- Click add vehicle and add your target's license plate
- Go to Payment cards and add a payment card
- All set! You are now able to intercept (and pay for) your victim's parking sessions in real-time, disclosing their location
3.7. TWINT+ / ParkingPay
Active in: 🇨🇭
CH Note: we were not able to test this application due to it only being available to Swiss citizens. The information in this section is based on public resources and will need to be confirmed by a local citizen. Mobile app: Android iOS Contact: [email protected] Steps to track a target:- Open the TWINT app and tap on TWINT+
- Choose "parking" and tap on the car symbol on the right
- Add your target's license plate
- Click on License Plate Recognition and activate it
- All set! You are now able to intercept (and pay for) your victim's parking sessions in real-time, disclosing their location
3.8. AENA Parking
Active in: 🇪🇸 ES Mobile app: Android iOS Contact: [email protected] Steps to track a target:- Register for AENA Club here
- Add the target's license plate here
- Add a payment method here
- Activate number plate payment for all locations here
- All set! You are now able to intercept (and pay for) your victim's parking sessions in real-time, disclosing their location
3.9. NCP (National Car Parks)
Active in: 🇬🇧 UK Mobile app (ParkPass): Android iOS Contact: [email protected] Steps to track a target:- Download & install the 'ParkPass' app on your mobile device
- In settings, go to payment details and add a card
- In settings, go to vehicles and add your target's VRN
- Toggle the 'Enable AutoPay' switch
- All set! You are now able to intercept (and pay for) your victim's parking sessions in real-time, disclosing their location
3.10. Various integrators
Some parking applications integrate with ANPR technologies implemented by other parking applications.
While these may still be vulnerable to the attacks described in "2.2. Trial-and-error attacks with free limited parking" and "2.3. Authentication by plate in parking apps", they are currently not listed as a processor of the data in NOTMYPLATE.
Examples include:
- 4411 (Q-Park integration)
- ParkMobile (Q-Park integration)
- ParkNow (Q-Park integration)
- KBC (Q-Park integration)
- ...
4. Conclusion
With nearly 4,000 affected locations across Western Europe and more than a million trackable parking spots in 10 different countries, it is getting increasingly harder to travel across Europe without the risk of exposing your location. During our tests, we were able to locate a target parking their vehicle more than 1,100km from their home, near the Spanish border.
While a driver may choose to avoid ANPR-based parking garages, it can be more difficult to completely avoid toll roads over longer distances. In Sweden and Norway Epass24 already automatically charges tolls to accounts with a user-supplied license plate, along with Ireland’s M50 and England’s M6.
As more than half of installations activated in the past three years, it is likely that we will see a rapid growth of B2C ANPR cameras in the months to come. Combined with urban mobility plans that typically strive to relocate cars from the street to dedicated parking garages, more vehicles will be registered by ANPR cameras in the future.
The fact that nearly a quarter of all vehicles were successfully tracked during this experiment shows that action needs to be taken as soon as possible. Parking apps should be made privacy-first, and should properly verify and inform data subjects as required by privacy laws.
On the drivers’ side, this should serve as a reminder that a license plate is a personal identifiable information record that should never be exposed to others online, e.g. on social media. This document is not a manifesto against technology, but rather a warning that convenience should not come at the cost of our privacy.
from Hacker News https://ift.tt/qEOjywa
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.